What Is a Security Operations Center (SOC)?

What is a security operations center?
A security operations center (SOC) is a command center facility in which a team of information technology (IT) professionals with expertise in information security (infosec) monitors, analyzes and protects an organization from cyberattacks.
In the SOC, internet traffic, networks, desktops, servers, endpoint devices, databases, applications and other systems are continuously monitored and analyzed for signs of a potential or actual security incident. SOC staff can work with other teams and departments but are typically self-contained with employees that have high-level IT and cybersecurity skills. Most SOCs function nonstop, with employees working in shifts using security tools to log activity, analyze anomalies and mitigate and eliminate cyberthreats and malware.
SOCs are an integral part an organization’s data protection strategy and minimizing the costs of a potential data breach. They help organizations respond to intrusions quickly while also improving detection and prevention processes.
Most large organizations have an in-house SOC in the IT department or another organization such as a network operations center (NOC). Companies with insufficient staff or resources to maintain a SOC themselves might outsource some or all SOC functions to a managed service provider or a cloud vendor that offers a hosted virtual SOC.
SOCs are commonly found in healthcare, education, banking and finance, insurance, e-commerce, government, military operations and advanced technology industries.
Who needs a security operations center?
Before establishing a SOC, an organization must align its security strategy with current business goals and programs. The purpose of the SOC is to protect an organization’s security posture by implementing systems to identify potential and real-time security threats.
When determining the need for a SOC, senior leadership might examine data from periodic risk assessments and other reports that focus on core needs, such as the following:
- Identifying requirements to maintain the company’s mission if a cyberattack occurs.
- Defining policies and procedures for managing cybersecurity operations and remediating cyberattacks if they occur.
- Establishing an incident response process for handling a cyber event.
- Documenting the infrastructure resources, systems and management tools needed to respond to a cyberattack.
- Identifying and training security teams responsible for identifying and responding to cyber events.
- Establishing a formal cybersecurity function with security professionals to prepare for and manage attacks via a SOC.
What does a security operations center do?
SOCs’ main focus is on threat detection, assessment and management. The work includes collecting data and analyzing it for suspicious activity. The goal is to make the entire organization more secure.
Raw security-focused data that SOC teams monitor is collected from firewalls, threat intelligence, intrusion prevention and detection systems, probes, and security information and event management or (SIEM) systems. Alerts can be set to notify team members if data is abnormal or displays indicators of compromise.
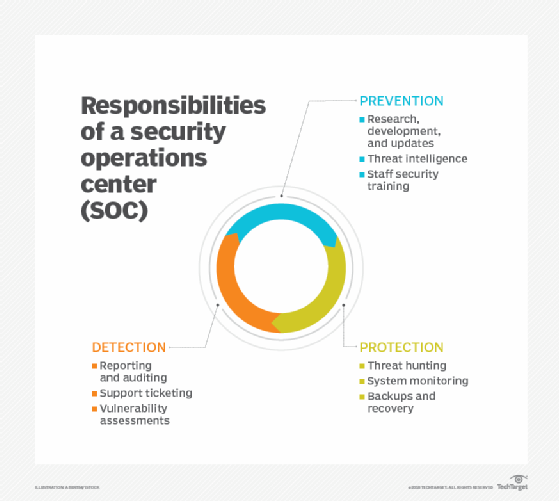
The following are the basic responsibilities of a SOC team:
- Asset discovery and management involves obtaining a high awareness of all tools, software, hardware and technologies the organization uses. These focus on ensuring all assets are working properly and are regularly patched and updated. SOC teams must also stay up to date on the most current cybersecurity technologies, attack signatures and other relevant data.
- Continuous behavioral monitoring requires examining all systems on a 24/7 basis. Continuous monitoring enables SOCs to place equal weight on reactive and proactive measures, so any irregularity is detected quickly. Behavioral models train data collection systems on what activities are suspicious and can be used to preclude false positives.
- Activity logs should log all communications and activity across an organization. This enables SOC teams to identify previous actions and situations that may have facilitated a breach.
- Alert severity ranking helps teams prioritize alerts. Teams must regularly rank cybersecurity threats based on occurrence probability and potential damages and to help with triage efforts when incidents occur.
- Defense development and evolution require teams to stay updated on potential threats and strategies. It includes creating an incident response plan to defend systems against new or ongoing attacks. Teams might need to adjust their plan when new information emerges.
- Incident recovery includes reconfiguring, updating or backing up systems and mission-critical data.
- Testing and exercising cybersecurity measures ensure that all resources assigned to cybersecurity are the most appropriate for the job. It also requires that cyberteam members know their roles and responsibilities in a breach.
- Compliance management means doing what’s necessary to follow regulatory and cybersecurity standards in carrying out cybersecurity activities. Typically, one team member oversees compliance duties.
- Documentation and reporting of cyber events are essential for subsequent review, training and audits.
- Evidence gathering for IT audits is important and requires having a principal repository of data relating to cyberactivities, cyberattacks and post-event reporting.
Additional SOC capabilities include reverse-engineering, forensic analysis, network telemetry and cryptanalysis based on the organization’s specific needs.
Building a winning SOC team
SOCs are staffed with a diverse set of individuals who play a role in managing security operations. Job titles and responsibilities found in a SOC include the following:
- SOC manager. This person directs the SOC’s daily operations and its cybersecurity team. They also provide updates to the organization’s executive staff.
- Incident responder. An incident responder handles successful attacks or breaches, doing what’s necessary to mitigate and remove the threat.
- Forensic investigator. This is the individual or group that identifies the root cause of an issue, locates the attack source and collects supporting evidence.
- Compliance analyst. This person ensures all SOC processes and employee actions meet compliance requirements.
- SOC security analyst. The person or people who review and organize security alerts by urgency and severity, and run regular vulnerability assessments. SOC analysts have skills such as knowledge of programming languages, cybersecurity systems, ransomware systems, administrative capabilities and security practices.
- Threat hunter. Also known as a threat analyst, this person reviews data the SOC collects to identify hard-to-detect threats. Resilience and penetration testing might be part of a threat hunting routine.
- Security engineer. This staffer develops and designs the systems or tools essential for effective intrusion detection and prevention, vulnerability assessments and event response management.

Types of security operations centers
An organization implementing a SOC can choose from several models, including the following:
- Dedicated or self-managed SOC. This model has an on-premises facility with in-house staff.
- Distributed SOC. This model is also known as a co-managed SOC. It has full- or part-time team members who are hired in-house to work alongside a third-party managed security service provider (MSSP).
- Managed SOC. This model has MSSPs providing all SOC services. Managed detection and response partners are another type of managed SOC.
- Command SOC. This model provides threat intelligence insights and security expertise to other, typically dedicated, SOCs. A command SOC isn’t involved in security operations or processes, just intelligence.
- Fusion center. This model oversees any security-focused facility or initiative, including other types of SOCs and IT departments. Fusion centers are considered advanced SOCs and work with other enterprise teams, such as IT operations, DevOps and product development.
- Multifunction SOC. This model has a dedicated facility and in-house staff, but its roles and responsibilities extend to other critical areas of IT management, such as NOCs.
- Virtual SOC. This model lacks a dedicated on-premises facility and can be enterprise-run or fully managed. An enterprise-run SOC is generally staffed by in-house employees or a mix of in-house, on-demand and cloud-provided employees. A fully managed, virtual SOC, also known as an outsourced SOC or SOC as a service, has no in-house staff.
- SOCaaS. This subscription-based or software-based model outsources some or all SOC functions to a cloud provider.
Security operations center best practices
There are several best practices for running a SOC. Success starts with selecting the optimal model for an organization, staffing the team with the best security specialists, and adopting the proper tools and technologies.
Next, establish policies and procedures for the SOC, ensuring they have senior management approval and comply with the organization’s standards and regulations. The SOC might provide important data needed when evaluating cybersecurity insurance.
Implement security orchestration, automation and response (SOAR) processes whenever possible. Combining the productivity of an automation tool with the technical skills of an analyst helps improve efficiency and turnaround times. It also maintains the SOC function without interruption.
SOCs rely heavily on the knowledge of cybersecurity team members. Managers should provide ongoing training to stay on top of emerging threats, cybersecurity incident reports and vulnerabilities. SOC monitoring tools should be updated and patched regularly to reflect any changes.
A SOC is only as effective as the strategies it has in place. Managers should implement operational protocols, specified in SOC policies. These should be strong enough to ensure a consistent, fast and effective response.
Other SOC best practices include the following:
- Periodic testing of systems and incident response activities.
- Obtaining security risk visibility across the business.
- Collecting as much relevant data as possible as often as possible.
- Taking advantage of data analytics.
- Developing scalable processes.
Artificial intelligence (AI) and machine learning functions are increasingly part of cybersecurity management systems. Adoption of AI functionality in a SOC is likely to improve its ability to identify potential attackers and defeat them before they can strike.
Benefits of a security operations center
When implemented correctly, a SOC can provide an organization with numerous benefits such as the following:
- Uninterrupted security monitoring and analysis for suspicious activity.
- Improved incident response times and practices.
- Reduced time frames between time of compromise and mean time to detect.
- Centralized software and hardware assets for a more holistic approach to security systems.
- Effective communication and collaboration.
- Minimized costs associated with cybersecurity incidents.
- Customers and employees who are more comfortable sharing sensitive information.
- More transparency and control over security operations.
- Established chain of control for data needed if an organization plans to prosecute those involved in a cybercrime.
- Improvements in the organization’s reputation.
Network operations center vs. security operations center
A NOC is similar to a SOC in that its basic responsibilities are to identify, investigate, rank and fix issues. A NOC manager or team lead oversees all employees and processes in the center. Most of the staff members are network and traffic engineers, some of whom might have more specialized or technical backgrounds to cover a diverse range of incidents.
Unlike in a SOC, a NOC team primarily handles issues related to network performance, reliability and availability. This includes implementing processes for network monitoring, device malfunctions and network configuration. A NOC is also in charge of ensuring the network meets service-level-agreement requirements, such as minimum downtime and network latency.
SOCs and NOCs respond to very different types of incidents. Network issues are typically operational events, such as a switching system malfunction, traffic congestion and a loss of transmission facilities.
By contrast, cybersecurity events come from sources both inside and outside the organization’s control. They use existing networks to gain unauthorized access to company resources. They can also involve social engineering attacks, using coercion or tricks to get people to share confidential information. Rogue employees, who present a serious security risk, especially if they know security access codes, are also under the SOC’s purview.
NOCs typically cover hardware and physical equipment repairs, software management, coordination with network carriers, internet service providers and utility companies.
NOCs are useful for organizations that rely on website accessibility and reliable internet connections, such as an e-commerce business. As such, it may be advantageous to collocate a SOC with a NOC.
Find out more about how generative AI is being used in security operations and how this might affect security operations centers.




