Corporate network security levels

Editor’s note: In the article, ScienceSoft’s certified ethical hacker Uladzislau Murashka explains when and for whom each of the three levels of corporate network security is appropriate. Read on for some useful hints about the protection of your corporate infrastructure. And if you think you need help with checking the effectiveness your IT protection, you are welcome to explore ScienceSoft’s offer in security testing services.
As cyberthreats are constantly evolving in complexity and volume, the battle against them implies ‘spreading’ the protection across all the systems in the corporate network – servers, databases, services, installed software, etc. What’s more, attention should be paid to ensuring that the company’s employees understand and follow cybersecurity principles, and will not (un)intentionally compromise the corporate network security with their actions.
However, cybersecurity measures applied inside the organization may differ depending on the company’s size, its financial capabilities, the industry it operates in (regulated or non-regulated), the information it has to deal with in the course of business activities, etc.

Bearing in mind these and other factors, we managed to determine three main cybersecurity protection levels. Depending on their complexity, these levels can be established with the assistance of a company’s IT department or a cybersecurity services provider.
Level 1 – minimal protection
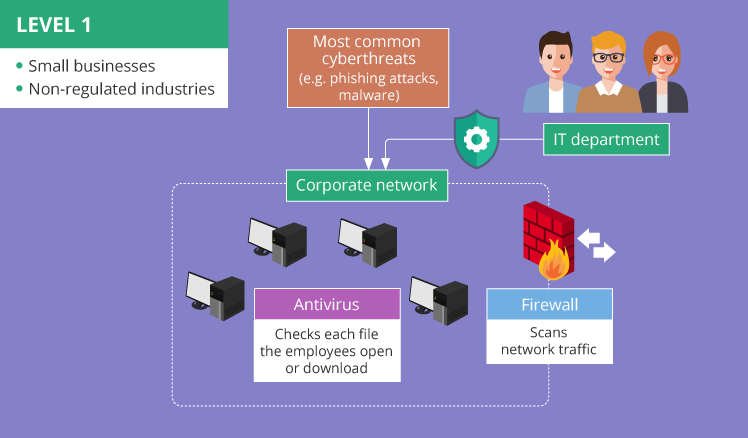
The key point of Level 1 cybersecurity is to ensure the protection of the corporate network from the most common cyberthreats, e.g., phishing attacks (links to malicious websites or downloads infected with viruses are attached to emails or instant messages and sent to a company’s employees) and malware (malicious software reaching a company’s network via internet or email and existing in the form of spyware, ransomware, browser hijackers, etc.).
Minimal protection applies to small businesses operating in non-regulated industries and having strictly limited financial resources. Small and not widely-known (at least not yet) companies that don’t deal with information valuable for hackers (e.g., customer personal data like credit card numbers, passwords, etc.) may hardly become targets of sophisticated cyberattacks like DDoS (Distributed Denial of Service) or spear phishing.
The minimum of cybersecurity measures essential for the implementation is a properly configured firewall protection working together with regularly updated antivirus software. Firewalls scan network traffic to detect anomalous packets or packet fragments. Antiviruses ensure protection from such cyberthreats as ransomware, worms, spyware, etc. by checking each file the employees open or download from the internet or other sources.
To apply these security measures, there’s no need in organizing a separate cybersecurity department. A company’s IT department can take responsibility for this, as implementing firewall protection, installing antivirus software and continuously maintaining their performance does not require cybersecurity-related skills.
Nevertheless, the protection level of a corporate network should be regularly checked. Conducting vulnerability assessment and penetration testing annually is enough for a small organization carrying out their business in a non-regulated industry. These cybersecurity services performed on an annual basis won’t result in heavy expenses for a company with a limited budget. At the same time, these activities can help system administrators to stay aware of occurring security weaknesses inside the company’s network.
Level 2 – advanced protection
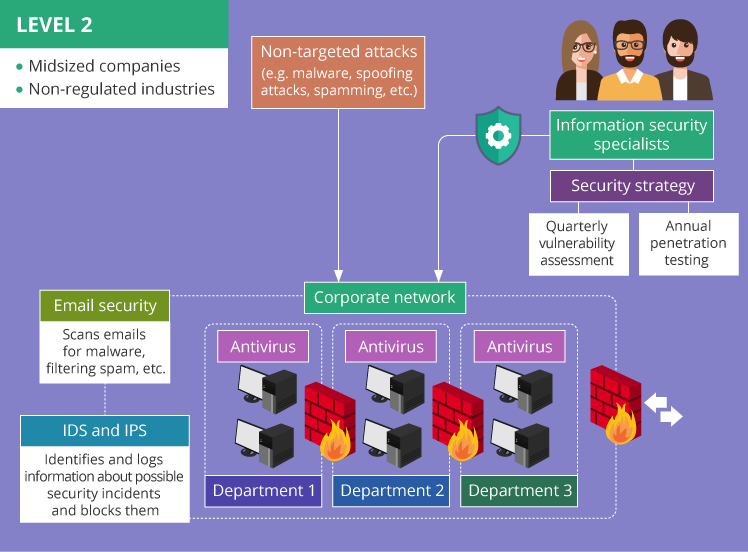
Level 2 cybersecurity ensures the protection of the corporate network from non-targeted attacks, e.g., malware sent to a range of email addresses, spoofing attacks, spamming, etc. In this case, attackers’ goal is to steal any valuable information from any IP address susceptible to known security weaknesses possibly existing in the corporate network.
The probability that midsized companies will fall victim to non-targeted attacks is great. Since such organizations have no need to comply with regulatory standards, they may be likely to neglect strong cybersecurity measures in their networks. Thus, they may be easy to compromise.
To ensure advanced protection of the corporate network, in addition to the elements of minimal protection – firewalls and antivirus – the following components should be applied:
- Email security implying a variety of techniques (scanning emails for malware, filtering spam, etc.) to keep corporate information secure both in the ‘internal’ and ‘external’ email communication from any cyberattack using email as an entry point (spyware, adware, etc.).
- Network segmentation, e.g., segmenting the network by departments with the segments connected via firewalls that do not allow malicious code or other threats to travel from one network segment to another. What’s more, network segmentation implies separating the network assets storing a company’s data from the outside-facing segments (web servers, proxy servers), thus reducing the risk of data loss.
- Intrusion detection (IDS) and intrusion prevention system (IPS) used to identify and log information about possible security incidents, block them before they spread across network environments, etc.
To maintain this level of network security, a company needs information security specialists responsible for detecting and managing cybersecurity risks, developing security procedures and policies, etc. For these purposes, the company may arrange their own information security department or turn to a managed security service provider (MSSP).
Organizing a separate information security department implies heavy expenses both on hiring an experienced security team and buying the necessary equipment and software. Working with an MSSP is a more cost-effective solution, which allows a company to maintain the focus on the primary business operations. Nevertheless, the company will still need an in-house security officer to coordinate the work with MSSP.
To control the efficiency of cybersecurity protection, a carefully designed security strategy should provide for quarterly vulnerability assessment and annual network penetration testing to detect, mitigate and manage cybersecurity risks. A company needs a cybersecurity strategy as it focuses on protecting the corporate network taking into account the staff using their personal mobile devices and laptops for business purposes (BYOD), wide use of cloud computing, etc. and provides direct guidance for company employees about acceptable behavior inside the corporate network.
Level 3 – maximal protection
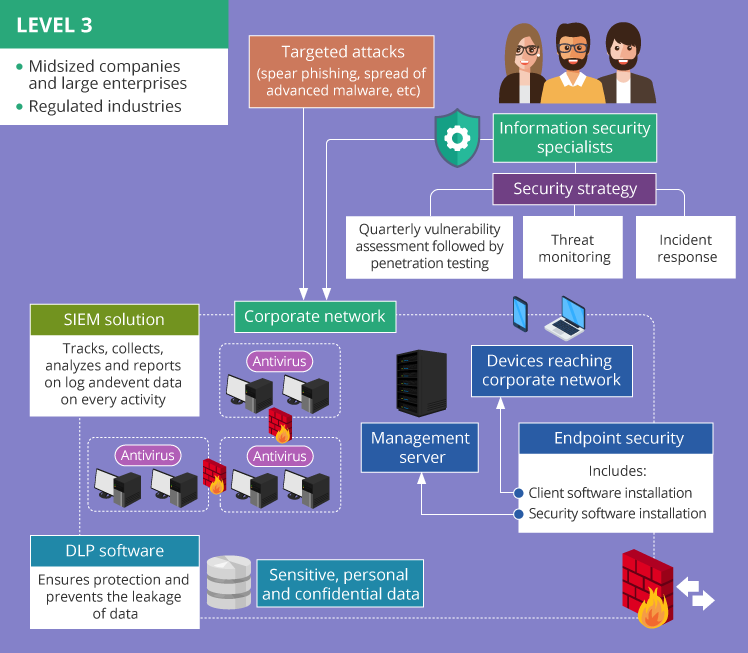
The key task of Level 3 cybersecurity is to ensure the protection of the corporate network from targeted attacks. This type of cyberattacks (spear phishing, the spread of advanced malware, etc.) implies specifically developed campaigns conducted against a particular organization.
Midsized companies and large enterprises operating in regulated industries, e.g., banking or healthcare, or government agencies usually become the victims of targeted attacks. This happens because the larger an organization is and the more data it has to protect (regulated personal data, patients’ healthcare records, bank accounts information, etc.), the more tangible the results of successful targeted attacks are.
Companies operating in regulated fields should pay the utmost attention to maintaining protection from cyberthreats while staying compliant with regulations and standards (HIPAA, PCI DSS, etc.). The following cybersecurity components may help to close all possible attack vectors:
- Endpoint security. This security method implies protecting access by each device (a smartphone, a laptop, etc.) reaching the corporate network and thus becoming a potential entry point for security threats. Usually, endpoint security includes the installation of special security software on a management server within the corporate network, together with the installation of client software on each device. The combination of these measures allows to monitor the activities users carry out when accessing the corporate network remotely from their smartphones, tablets, and other devices. Therefore, the company gets better real-time visibility over the entire range of potential security threats they might have to deal with.
- Data loss prevention (DLP). Applying this measure is extremely important within an enterprise engaged in the financial or healthcare sector. DLP software ensures protection and prevents the leakage of sensitive, personal and confidential data, e.g., clients’ credit card numbers, social security numbers, etc. providing DLP administrators with complete control over the types of data that can be transferred outside the corporate network. DLP may deny the attempts to forward any business email outside the corporate domain, upload corporate files to open-source cloud storages, etc.
- Security information and event management (SIEM). SIEM solutions track, collect, analyze and report on log and event data on every activity happening within the IT environment, which allows avoiding “I-have-no-idea-what-happened” situations in case the company’s network gets hacked. Among SIEM benefits are centralizing collected log data, providing support to meet the requirements of PCI DSS, HIPAA and other regulations, ensuring a real-time incident response.
To operate with the mentioned security solutions properly, the combination of the efforts of a separate information security department and the help of an MSSP will serve the best. For many companies, giving an MSSP total access and control over sensitive data, customer personal identifiable information, etc. seems rather risky, especially from the security compliance perspective. However, signing a detailed SLA with a cybersecurity services company and delegating a part of cyberprotection responsibilities to an external MSSP makes sense. It allows the enterprises to get 24/7 security state monitoring and reporting and reduce their expenses on cybersecurity protection at the same time.
Among the necessary cybersecurity measures are developing and maintaining a security strategy, conducting vulnerability assessment followed by penetration testing quarterly (should better be carried out before each audit check to stay compliant with standards and regulations), ensuring a constant threat monitoring, and organizing a structured incident response (IR).
Threat monitoring involves constant monitoring of the corporate network and the endpoints (servers, wireless devices, mobile devices, etc.) for the signs of cybersecurity threats, e.g., intrusion or data exfiltration attempts. Nowadays, threat monitoring is becoming even more important with the tendency at the enterprises to hire employees remotely and apply BYOD policy, which puts the protection of the corporate data and sensitive information under an additional risk.
Incident response (IR) deals with the situations when security breaches have already occurred. Thus, a company needs a special in-house or outsourced team prepared for the incidents, ready to detect actual events, find the causes and respond to cybersecurity threats with the least possible damage and the minimum time needed to recover from the attack. IR activities prevent small issues from transforming into bigger ones, such as data breach or system outage.
Cloud assets protection
Companies should give special attention to the protection of their cloud assets. Nowadays, storing business-critical data in the cloud becomes a common practice. Deciding on cloud computing makes sense as it allows enterprises to save costs and increase the efficiency of the business operations they carry out.
However, cloud environments represent relatively new areas for the security teams who need to organize and maintain the cybersecurity measures inside the corporate network. It also leads to new security challenges, as a “cloud nature” implies the lack of control for system administrators over the resources a company uses and the data they store in the cloud.
Cybersecurity specialists apply different strategies to protect cloud assets depending on a cloud model.
Infrastructure-as-a-Service (IaaS) and platform-as-a-service (PaaS)
In both cases, the cybersecurity strategy is similar to the approach for securing an on-premises corporate network. The difference lies in a ‘remoteness factor.’ The primary task of a company is to select a reliable IaaS/PaaS provider, get the servers in the cloud they offer, and establish an appropriate level of control over the provided virtual machines. There are best practices that can be applied to ensure IaaS/PaaS security, for example, ensuring the proper encryption of the data stored and sent to a third-party cloud, monitoring network traffic for malicious activities, regularly conducting data backup, etc.
Some vendors of IaaS or PaaS solutions provide their customers with ‘built-in’ cybersecurity services as well, but it’s not a common practice. For instance, Microsoft Azure offers the clients a variety of ways to protect workloads in the cloud, secure the apps from common vulnerabilities, etc. Amazon Web Services (AWS) represents another cloud services vendor providing their customers with applied cloud security measures (built-in firewalls, encryption capabilities, etc.), security assessment services for detecting cybersecurity weaknesses, identity and access management to define the users’ access to AWS resources, etc.
Software-as-a-Service (SaaS)
In this case, a SaaS vendor takes the responsibilities for building, hosting and securing software they offer. However, a company still have some work to do to ensure the security of the solution. They need to focus on managing access to applications for their employees taking into account the departments they work in, their positions, etc. Thus, the primary task of the security officers of the company is to establish user access control, i.e., configure the settings correctly.
Office 365 represents an example of a cloud solution with layered security. The cybersecurity features built in it allow continuously monitoring datacenters, identifying and preventing malicious attempts to access personal or sensitive information, encrypting the stored and transmitted data, using antivirus and antispam protection to stay secure from cybersecurity threats coming to the corporate network from the outside, etc.
In summation
Corporate network security is not something that can be organized according to a general pattern equally suitable for any company. The choice of cybersecurity activities should depend on the size of a company, their budget, and the area they operate in.
To ensure cyberprotection of a small corporate network, if there is no necessity to secure their customers’ personal or financial data, applying firewall protection and antiviruses may be quite enough. However, if a company takes a relatively significant place in the area they operate in and may easily become a target of cyberattacks, they must be ready to extend the cybersecurity measures and apply email security, network segmentation, endpoint security, etc. Installing DLP and SIEM systems may also become a must-do, especially for organizations carrying out their activities in regulated industries.
To maintain the chosen cybersecurity level, a company should conduct network vulnerability assessment and penetration testing on a regular basis.




